You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
How to block IPs with Brute Force Monitor in DirectAdmin using CSF
- Thread starter zEitEr
- Start date
Develop
Verified User
Test (off)= 0
Chain num pkts bytes target prot opt in out source destination
DENYIN 63 0 0 DROP tcp -- !lo * 78.xxx.88.xx 0.0.0.0/0 tcp dpt:20
DENYIN 64 13 784 DROP tcp -- !lo * 78.xxx.88.xx 0.0.0.0/0 tcp dpt:21
Chain num pkts bytes target prot opt in out source destination
DENYIN 63 0 0 DROP tcp -- !lo * 78.xxx.88.xx 0.0.0.0/0 tcp dpt:20
DENYIN 64 13 784 DROP tcp -- !lo * 78.xxx.88.xx 0.0.0.0/0 tcp dpt:21
It's working, and blocking access only to attacked port, more reading:
https://forum.directadmin.com/showthread.php?t=44839&p=272598#post272598
https://forum.directadmin.com/showthread.php?t=44839&p=272598#post272598
Develop
Verified User
My old system settings for CSF was blocked IP for all. Example wrong pass login roundcube, on mobil device, ftp, BFA etc.
Sometimes CSF bloked me when I try to login abc.com:2222. And I unblocked IP's on CSF.
Now I consifer; how to unblock IP, if blocked somewhere directadmin or csf when I need to unblock it.
Sometimes CSF bloked me when I try to login abc.com:2222. And I unblocked IP's on CSF.
Now I consifer; how to unblock IP, if blocked somewhere directadmin or csf when I need to unblock it.
Develop
Verified User
Thank you for all.
Tested and working very well.
And the last question is CSF blocks port 5-10 wrong login attempt can I make it 20 or more?
Tested and working very well.
And the last question is CSF blocks port 5-10 wrong login attempt can I make it 20 or more?
When using Directamin BFM and CSF it's highly suggested to disable login failure detector in CSF. More reading: https://forum.directadmin.com/showthread.php?t=44839&p=272633#post272633
Develop
Verified User
Let the login failure check to BFM isn't it?
New CSF:
LF_TRIGGER = "0"
LF_SSHD = "0"
LF_FTPD = "0"
LF_SMTPAUTH = "0"
LF_EXIMSYNTAX = "0"
LF_POP3D = "0"
LF_IMAPD = "0"
LF_HTACCESS = "0"
LF_MODSEC = "0"
LF_DIRECTADMIN = "0"
Thanks....
New CSF:
LF_TRIGGER = "0"
LF_SSHD = "0"
LF_FTPD = "0"
LF_SMTPAUTH = "0"
LF_EXIMSYNTAX = "0"
LF_POP3D = "0"
LF_IMAPD = "0"
LF_HTACCESS = "0"
LF_MODSEC = "0"
LF_DIRECTADMIN = "0"
Thanks....
To make Directadmin's BFM compatible with CSF you should do the following:
...
Dear Forum Users,
Thanks for this post, I have installed it - it works fine for me. I use the automatic adding script (brute_force_notice_ip.sh)
However, I really want to tweak it, I use this version of block_ip.sh - 0.1.6
Q1:
How does this file work:
EF="/root/exempt_ips.txt";
Is this just plain text, add each IP on a new line? Anyone got an example?
Q2:
SLF="/usr/local/directadmin/data/admin/brute_skip.list";
I don't seem to have this file? Where can I get this file? (also tried "locate", it was not found on my server).
Q3:
TTL, where does it come from? All blocks now have are temporary of 3600 seconds. In the file I see this:
TTL=`/usr/local/directadmin/directadmin c | grep unblock_brute_ip_time= | cut -d\= -f2`;
TTL=$((TTL*3*60)); # It is Directadmin which unblocks IP, so we need to have enough long TTL
# so that Directadmin have a chance to unblock it
# Additionaly convert minutes to seconds *60
I don't think I can find the "unblock_brute_ip_time" in this file: /usr/local/directadmin/directadmin
Q4:
I figured that this script/scripts are using the Security values under CMD_ADMIN_SETTINGS
Any advice on this?
What I want - if an IP get's blocked, I like to see the it in the log for about 7 days.
These are my current settings:
Prevent 127.0.0.1 from being Blacklisted = Yes
Time before failed login count resets = 1200
Remove an IP from the blacklist after = 2880
Parse service logs for brute force attacks = Yes
Notify Admins after an IP has = 200
Notify Admins after a User has = 200
Remove an IP from the BF blacklist after = 0
Reset count of IP/User failed attempts = 168
Clear failed login attempts from log = 7
Scan for WordPress attacks = All logs
I can't seem to find the value 3600 (TTL)?
At this moment, a block will be temporary for 3600 (1 hour) - but some IP's will be blocked directly again, after this 1 hour period, for failing 1 more login. (ei 200 failed logins > block 1 hour> 1 hour later > 201st failed login > blocked again by 1 hour > etc.).
I really like to increase this 3600 seconds (TTL), any advice on this?
Thanks for reading!
Q1:
How does this file work:
EF="/root/exempt_ips.txt";
The file is fully managed by Directadmin you should not touch it.
Q2:
SLF="/usr/local/directadmin/data/admin/brute_skip.list";
I don't seem to have this file? Where can I get this file? (also tried "locate", it was not found on my server).
The file is fully managed by Directadmin you should not touch it manually. You can add IPs into the file in Directadmin at admin level (Brute Force Monitor /CMD_BRUTE_FORCE_MONITOR)
Q3:
TTL, where does it come from? All blocks now have are temporary of 3600 seconds. In the file I see this:
TTL=`/usr/local/directadmin/directadmin c | grep unblock_brute_ip_time= | cut -d\= -f2`;
TTL=$((TTL*3*60)); # It is Directadmin which unblocks IP, so we need to have enough long TTL
# so that Directadmin have a chance to unblock it
# Additionaly convert minutes to seconds *60
I don't think I can find the "unblock_brute_ip_time" in this file: /usr/local/directadmin/directadmin
It's a binary, you should not try to find anything in it.
Q4:
I figured that this script/scripts are using the Security values under CMD_ADMIN_SETTINGS
Any advice on this?
What I want - if an IP get's blocked, I like to see the it in the log for about 7 days.
These are my current settings:
Prevent 127.0.0.1 from being Blacklisted = Yes
Time before failed login count resets = 1200
Remove an IP from the blacklist after = 2880
Parse service logs for brute force attacks = Yes
Notify Admins after an IP has = 200
Notify Admins after a User has = 200
Remove an IP from the BF blacklist after = 0
Reset count of IP/User failed attempts = 168
Clear failed login attempts from log = 7
Scan for WordPress attacks = All logs
I can't seem to find the value 3600 (TTL)?
At this moment, a block will be temporary for 3600 (1 hour) - but some IP's will be blocked directly again, after this 1 hour period, for failing 1 more login. (ei 200 failed logins > block 1 hour> 1 hour later > 201st failed login > blocked again by 1 hour > etc.).
I really like to increase this 3600 seconds (TTL), any advice on this?
Thanks for reading!
Change zero 0 to 3600 if you want an IP be removed after 3600 minutes, or to 60 if you want an IP be removed from ban after an 60 minutes (1 hour). You have now:
Remove an IP from the BF blacklist after = 0
Thanks for all the help.
Still I can't seem to alter this:
Whenever a IP gets blocked, this is the value in CSF (fictional IP):
Temporary Blocks: IP:12.34.56.78 Port:110 Dir:inout TTL:3600 (Blocked port 110 with Directadmin Brute Force Manager)
So it will be blocked only for 3600 seconds. Is there anyway to increase this temp block to 1 day (86 400 seconds).
Thanks again!
Still I can't seem to alter this:
Whenever a IP gets blocked, this is the value in CSF (fictional IP):
Temporary Blocks: IP:12.34.56.78 Port:110 Dir:inout TTL:3600 (Blocked port 110 with Directadmin Brute Force Manager)
So it will be blocked only for 3600 seconds. Is there anyway to increase this temp block to 1 day (86 400 seconds).
Thanks again!
mohammad.983
Verified User
- Joined
- Jun 26, 2015
- Messages
- 35
Does it work on centos 7 ?
SeLLeRoNe
Super Moderator
Yes
Best regards
Best regards
Does it work on centos 7 ?
It works on all OS versions which are officially supported both by Directadmin and CSF/LFD.
That depends on your settings in Directadmin. It's on admin level
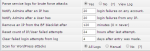
I usually set it to 20-30, so an IP gets blocked after 20-30 attempts. Please note Directadmin does not allow to set different values depending on a service under an attack.
Full instructions on one page can be found here: https://help.poralix.com/articles/how-to-block-ips-with-csf-directadmin-bfm

I usually set it to 20-30, so an IP gets blocked after 20-30 attempts. Please note Directadmin does not allow to set different values depending on a service under an attack.
Full instructions on one page can be found here: https://help.poralix.com/articles/how-to-block-ips-with-csf-directadmin-bfm
More automation is added now. Auto-installation with the help of the script:
Code:
cd ~
wget -O csf-bfm-install.sh https://raw.githubusercontent.com/poralix/directadmin-bfm-csf/master/install.sh
chmod 700 csf-bfm-install.sh
./csf-bfm-install.sh