Hi all.,
I want to discuss to anyone who have experience about this.
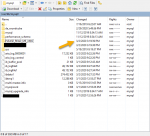
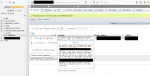
my customer got database gone. by hacker big database around 100g
absolutely hacker need bitcoin from me, see photo
How to protect ?
I want to discuss to anyone who have experience about this.
my customer got database gone. by hacker big database around 100g
absolutely hacker need bitcoin from me, see photo
How to protect ?