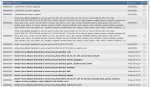
Hello,
A few days ago my DirectAdmin has been automatically updated to version 1.39.1.
With DirectAdmin 1.39.1 i receive everyday hundreds of emails with object 'Brute-Force Attack detected in service log'.
I think it is a new feature of DirectAdmin 1.39.1, but i receive too many of these emails per day and this is becoming a problem for me.
What is the utility of these emails?
How can i block the sending of these emails?
Is there anyone that can help me, please?
Thank you in advance.
Regards,
George
A few days ago my DirectAdmin has been automatically updated to version 1.39.1.
With DirectAdmin 1.39.1 i receive everyday hundreds of emails with object 'Brute-Force Attack detected in service log'.
I think it is a new feature of DirectAdmin 1.39.1, but i receive too many of these emails per day and this is becoming a problem for me.
What is the utility of these emails?
How can i block the sending of these emails?
Is there anyone that can help me, please?
Thank you in advance.
Regards,
George