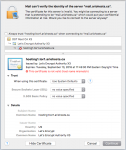
I've got Let's Encrypt certificates set up for hostname.mydomain.com as well as www.mydomain.com and mail.mydomain.com:
If I browse to https://mydomain.com, the page is secured. If I browse to https://www.mydomain.com or https://mail.mydomain.com, I get a certificate warning saying the cert for those hosts are invalid. I've attached a screen shot of the warning.
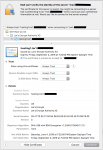
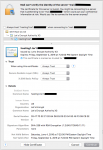
I've tried to revoke the certificate and re-request it, renew it, re-request it, but no matter what I try it's still invalid.
One thing I did notice is that in the certificate warning, the date in the certificate details is the same even after I revoke or renew it or request it, so it seems clear that through whatever process, the new certificate is not being copied to nginx or dovecom/exim. I tried to manually delete those certificates and re-requested the certs, but that doesn't copy the certs back to nginx or dovecot/exim.
Is my hunch correct? Is the issue that the old certificate isn't properly getting overwritten with the new one after requesting the new certificate after adding the new DNS: entries?
Any ideas on how I can force that to happen?
Thanks!
Code:
# more /usr/local/directadmin/conf/ca.san_config
[ req_distinguished_name ]
CN = hosting1.tor1.mydomain.com
[ req ]
distinguished_name = req_distinguished_name
[SAN]
subjectAltName=DNS:hosting1.tor1.mydomain.com
# more /usr/local/directadmin/data/users/admin/domains/mydomain.com.san_config
[ req ]
default_bits = 4096
default_keyfile = keyfile.pem
distinguished_name = req_distinguished_name
attributes = req_attributes
prompt = no
output_password = bogus
[ req_distinguished_name ]
C = CA
ST = Ontario
L = Toronto
O = My Domain
CN = mydomain.com
emailAddress = [email protected]
[ req_attributes ]
[ SAN ]
subjectAltName=DNS:mydomain.com, DNS:www.mydomain.com, DNS:mail.mydomain.comIf I browse to https://mydomain.com, the page is secured. If I browse to https://www.mydomain.com or https://mail.mydomain.com, I get a certificate warning saying the cert for those hosts are invalid. I've attached a screen shot of the warning.

I've tried to revoke the certificate and re-request it, renew it, re-request it, but no matter what I try it's still invalid.
Code:
# ./letsencrypt.sh revoke mydomain.com 4096
Certificate has been successfully revoked.
# ./letsencrypt.sh reqeust mydomain.com 4096
Getting challenge for mydomain.com from acme-server...
Waiting for domain verification...
Challenge is valid.
Getting challenge for www.mydomain.com from acme-server...
Waiting for domain verification...
Challenge is valid.
Getting challenge for mail.mydomain.com from acme-server...
Waiting for domain verification...
Challenge is valid.
Generating 4096 bit RSA key for mydomain.com...
openssl genrsa 4096 > "/usr/local/directadmin/data/users/admin/domains/mydomain.com.key.new"
Generating RSA private key, 4096 bit long modulus
...............................++
.++
e is 65537 (0x10001)
Certificate for mydomain.com has been created successfully!
#One thing I did notice is that in the certificate warning, the date in the certificate details is the same even after I revoke or renew it or request it, so it seems clear that through whatever process, the new certificate is not being copied to nginx or dovecom/exim. I tried to manually delete those certificates and re-requested the certs, but that doesn't copy the certs back to nginx or dovecot/exim.
Is my hunch correct? Is the issue that the old certificate isn't properly getting overwritten with the new one after requesting the new certificate after adding the new DNS: entries?
Any ideas on how I can force that to happen?
Thanks!