Richard G
Verified User
Anyone a clue?
Since like a couple of weeks almost daily on at least 2 servers I get messages like below from CSF firewall.
Never had them before, but seems amazonaws ip's are using massive connections, over 1000 often, but often a lot of time_wait connections like this:
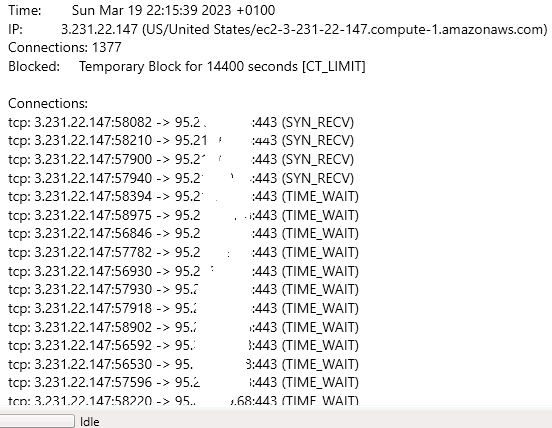
In this case 1377 connections, it's always to port 443, so one would think to a website.
But when I do a grep on the ip, I can't find anything in the syslog or httpd logs or domain logs.
In /var/log/httpd/domains I tried like
It seems only the firewall sees this and blocks this, so I don't know where this is going.
And this is multiple times a day and from multiple amazonews ip addresses.
Now I can disable these mails, but amazonaws is the only one causing these, so this seems not right. I can't fill in an abuse report, because they want a piece of the according log, which I don't have, because I can't find anything.
Does anyone have an idea where to look for?
Since like a couple of weeks almost daily on at least 2 servers I get messages like below from CSF firewall.
Never had them before, but seems amazonaws ip's are using massive connections, over 1000 often, but often a lot of time_wait connections like this:
In this case 1377 connections, it's always to port 443, so one would think to a website.
But when I do a grep on the ip, I can't find anything in the syslog or httpd logs or domain logs.
In /var/log/httpd/domains I tried like
cat * | grep 3.231.22.147 but nothing. Same in /var/log or /var/log/directadmin. Only in /var/log I get an output from lfd.log.Mar 19 22:15:39 server23 lfd[30687]: (CT) IP 3.231.22.147 (US/United States/ec2-3-231-22-147.compute-1.amazonaws.com) found to have 1377 connections - *Blocked in csf* for 14400 secs [CT_LIMIT]
It seems only the firewall sees this and blocks this, so I don't know where this is going.
And this is multiple times a day and from multiple amazonews ip addresses.
Now I can disable these mails, but amazonaws is the only one causing these, so this seems not right. I can't fill in an abuse report, because they want a piece of the according log, which I don't have, because I can't find anything.
Does anyone have an idea where to look for?