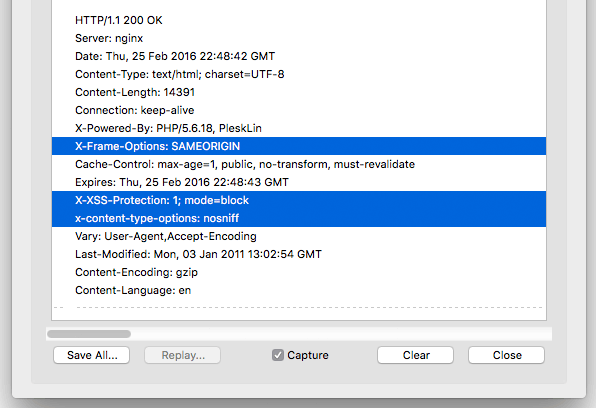
Got one email like this.??? So how can i review and block this type of vulnerability
Hi Team.
I am a security researcher and I have found a bug in your website https://abcs.com/
The details of it are as follows:-
CLICK-JACKING.
Description :
Click-jacking, also known as a "UI redress attack" is when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when they were intending to click on the top level page. Thus, the attacker is "hijacking" clicks meant for their page and routing them to another page, most likely owned by another application, domain, or both.
Using a similar technique, keystrokes can also be hijacked. With a carefully crafted combination of style-sheets, I-frames, and text boxes, a user can be led to believe they are typing in the password to their email or bank account, but are instead typing into an invisible frame controlled by the attacker.
Impacts:
1. Tricking a user into unknowingly clicking on things and then gaining access to his account
2. An attacker can gain access to the credentials of users and use those credentials for booking and payment.
3. Adding events to their profile they are interested in attending.
4. editing their star rating on reviews
5. Using their bank account details to books in hotels whereas the bill will go to their bank account.
6. Bookmarking unwanted business.
POC:
<html>
<head>
</head>
<body>
<h1>Click-Jacking In Your Site</h1>
<iframe src=" https://abcs.com/clients/clientarea.php "height="800" width="1300">
</iframe>
</body>
</html>
Waiting for your reply.
Hi Team.
I am a security researcher and I have found a bug in your website https://abcs.com/
The details of it are as follows:-
CLICK-JACKING.
Description :
Click-jacking, also known as a "UI redress attack" is when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when they were intending to click on the top level page. Thus, the attacker is "hijacking" clicks meant for their page and routing them to another page, most likely owned by another application, domain, or both.
Using a similar technique, keystrokes can also be hijacked. With a carefully crafted combination of style-sheets, I-frames, and text boxes, a user can be led to believe they are typing in the password to their email or bank account, but are instead typing into an invisible frame controlled by the attacker.
Impacts:
1. Tricking a user into unknowingly clicking on things and then gaining access to his account
2. An attacker can gain access to the credentials of users and use those credentials for booking and payment.
3. Adding events to their profile they are interested in attending.
4. editing their star rating on reviews
5. Using their bank account details to books in hotels whereas the bill will go to their bank account.
6. Bookmarking unwanted business.
POC:
<html>
<head>
</head>
<body>
<h1>Click-Jacking In Your Site</h1>
<iframe src=" https://abcs.com/clients/clientarea.php "height="800" width="1300">
</iframe>
</body>
</html>
Waiting for your reply.