France Presern
New member
- Joined
- Oct 17, 2016
- Messages
- 2
Hi.
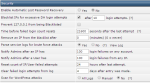
We are using DirectAdmin (version 1.50.1) and we installed CSF to use for brute-force protection for exim2, proftpd, ... We followed (to the letter) the instructions found at https://help.poralix.com/articles/how-to-block-ips-with-csf-directadmin-bfm . We are getting the brute force attempt notifications via e-mail (with subject New Message: Brute-Force Attack detected in service log from IP(s) ), but the attackers don't get blocked. According to configuration, the attackers should get blocked after 10 failed attempts but don't get even after 300+ attempts.
There is user interface for Brute Force Monitor in DirectAdmin. It is working in every aspect (it lists all the failed/brute force attempts and allows manual blocking of the attacking IPs) but automatic blocking.
Is there a step missing on https://help.poralix.com/articles/how-to-block-ips-with-csf-directadmin-bfm ? How can we fix it?
Thank you and best regards,
F.
We are using DirectAdmin (version 1.50.1) and we installed CSF to use for brute-force protection for exim2, proftpd, ... We followed (to the letter) the instructions found at https://help.poralix.com/articles/how-to-block-ips-with-csf-directadmin-bfm . We are getting the brute force attempt notifications via e-mail (with subject New Message: Brute-Force Attack detected in service log from IP(s) ), but the attackers don't get blocked. According to configuration, the attackers should get blocked after 10 failed attempts but don't get even after 300+ attempts.
There is user interface for Brute Force Monitor in DirectAdmin. It is working in every aspect (it lists all the failed/brute force attempts and allows manual blocking of the attacking IPs) but automatic blocking.
Is there a step missing on https://help.poralix.com/articles/how-to-block-ips-with-csf-directadmin-bfm ? How can we fix it?
Thank you and best regards,
F.