Q4:
I figured that this script/scripts are using the Security values under CMD_ADMIN_SETTINGS
Any advice on this?
What I want - if an IP get's blocked, I like to see the it in the log for about 7 days.
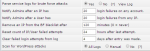
These are my current settings:
Prevent 127.0.0.1 from being Blacklisted = Yes
Time before failed login count resets = 1200
Remove an IP from the blacklist after = 2880
Parse service logs for brute force attacks = Yes
Notify Admins after an IP has = 200
Notify Admins after a User has = 200
Remove an IP from the BF blacklist after = 0
Reset count of IP/User failed attempts = 168
Clear failed login attempts from log = 7
Scan for WordPress attacks = All logs
I can't seem to find the value 3600 (TTL)?
At this moment, a block will be temporary for 3600 (1 hour) - but some IP's will be blocked directly again, after this 1 hour period, for failing 1 more login. (ei 200 failed logins > block 1 hour> 1 hour later > 201st failed login > blocked again by 1 hour > etc.).
I really like to increase this 3600 seconds (TTL), any advice on this?
Thanks for reading!