patrickkasie
Verified User
Dear DA forum,
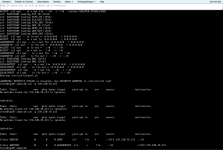
In the screenshots, I may have found a bug with CSF in CentOS7 using DirectAdmin. I can still access the website that's on the server which I want it to ban me.
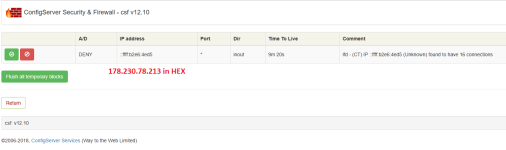
The CT_LIMIT is set at 15, so the IP address got banned very quickly, on purpose, as I want to test if the automated temp bans is working. It doesn't work though. The IP4 address has been placed in the IP6tables as seen in the screenshot above. Not only that, it also uses a translated IP6 to IP4 temp ban as seen in the 2nd screenshot. This only happens on CentOS7 though, and it does not seem to have this issue on AlmaLinux 8, and only if you ONLY have an IP4 available, not both IP4 and IP6
When using the following line, CSF does correctly ban both the IP4 address and IP6 address independently (using /etc/hosts to let this test run on IP6 and then IP4 when the IP6 address got banned)
ab -n 200 -c 31 https://www.costas-casas.com/marbel...oha-golf-stylishly-renovated-townhouse-182555
Using csf -d 178.230.78.213 works, I've just tested this. However, using the automated temp ban provided by CSF does not work upon tripping the CT_LIMIT of 15. I have the following values that seem relevant to me for this option:
LF_IPSET was on 1, I've set it to 0 as per recommendation by ChatGPT, Claude and Gemini and that's when I started writing this post when it still didn't work.
I've tried using a work around by using /etc/csf/csfpost.sh and making it executable, then csf -r. It only acts when you manually run csf -d as root though and not an automatic temp bans it seems. This is the code:
As a last ditch effort, I'm considering making a cronjob that checks every minute for a tempban and then permanently banning that IP4 using csf -d IP and then taking it out of the tempban and logging it, however the IP address may be formatted.
I have tried on other CentOS7 servers, I can't seem to trip the CT limit because I don't have any other heavy applications on other servers, so I can't say if it's universal or just unique to VPS07.
When using the following line, CSF does correctly ban both the IP4 address and IP6 address independently (using /etc/hosts to let this test run on IP6 and then IP4 when the IP6 address got banned)
ab -n 200 -c 31 https://www.costas-casas.com/marbel...oha-golf-stylishly-renovated-townhouse-182555
Kind regards,
Patrick
In the screenshots, I may have found a bug with CSF in CentOS7 using DirectAdmin. I can still access the website that's on the server which I want it to ban me.
The CT_LIMIT is set at 15, so the IP address got banned very quickly, on purpose, as I want to test if the automated temp bans is working. It doesn't work though. The IP4 address has been placed in the IP6tables as seen in the screenshot above. Not only that, it also uses a translated IP6 to IP4 temp ban as seen in the 2nd screenshot. This only happens on CentOS7 though, and it does not seem to have this issue on AlmaLinux 8, and only if you ONLY have an IP4 available, not both IP4 and IP6
When using the following line, CSF does correctly ban both the IP4 address and IP6 address independently (using /etc/hosts to let this test run on IP6 and then IP4 when the IP6 address got banned)
ab -n 200 -c 31 https://www.costas-casas.com/marbel...oha-golf-stylishly-renovated-townhouse-182555
Using csf -d 178.230.78.213 works, I've just tested this. However, using the automated temp ban provided by CSF does not work upon tripping the CT_LIMIT of 15. I have the following values that seem relevant to me for this option:
Code:
LF_IPSET = "0"
DENY_IP_LIMIT = "2000"
CT_LIMIT = "15"
CT_INTERVAL = "10"
CT_BLOCK_TIME = "600"
CT_SKIP_TIME_WAIT = "1"
CONNLIMIT = "80;50,443;50"
PORTFLOOD = ""LF_IPSET was on 1, I've set it to 0 as per recommendation by ChatGPT, Claude and Gemini and that's when I started writing this post when it still didn't work.
I've tried using a work around by using /etc/csf/csfpost.sh and making it executable, then csf -r. It only acts when you manually run csf -d as root though and not an automatic temp bans it seems. This is the code:
Code:
#!/bin/bash
ACTION="$1"
IP="$2"
LOG_FILE="/var/log/csf_mirror.log"
log() {
echo "$(date '+%Y-%m-%d %H:%M:%S') [csfpost] $1" >> "$LOG_FILE"
}
if [[ "$ACTION" == "deny" && "$IP" =~ ^::ffff: ]]; then
RAW=$(echo "$IP" | sed 's/.*::ffff://')
# Case 1: Already dotted IPv4
if [[ "$RAW" =~ ^[0-9]+\.[0-9]+\.[0-9]+\.[0-9]+$ ]]; then
IPV4="$RAW"
# Case 2: Hexadecimal format
elif [[ "$RAW" =~ ^[0-9a-fA-F]+:[0-9a-fA-F]+$ ]]; then
HEX=$(printf "%04x%04x" 0x${RAW/:/ 0x})
IPV4=$(printf "%d.%d.%d.%d" 0x${HEX:0:2} 0x${HEX:2:2} 0x${HEX:4:2} 0x${HEX:6:2})
else
log "Unsupported address format for IP: $IP"
exit 1
fi
if ! csf -g "$IPV4" | grep -q "DENY"; then
csf -d "$IPV4" "Auto-mirrored IPv4 ban from $IP"
log "Mirrored ban: $IP (IPv6-mapped) $IPV4 (IPv4)"
else
log "Already banned: $IPV4 skipping"
fi
fiAs a last ditch effort, I'm considering making a cronjob that checks every minute for a tempban and then permanently banning that IP4 using csf -d IP and then taking it out of the tempban and logging it, however the IP address may be formatted.
I have tried on other CentOS7 servers, I can't seem to trip the CT limit because I don't have any other heavy applications on other servers, so I can't say if it's universal or just unique to VPS07.
When using the following line, CSF does correctly ban both the IP4 address and IP6 address independently (using /etc/hosts to let this test run on IP6 and then IP4 when the IP6 address got banned)
ab -n 200 -c 31 https://www.costas-casas.com/marbel...oha-golf-stylishly-renovated-townhouse-182555
Kind regards,
Patrick