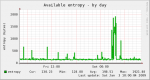
I manage a headless Centos52 box with DA. The current config is: 2.6.18-92.1.22.el5, apache 2.2.11, mysql 5.0.67, php 5.2.8, exim 4.69, dovecot 1.1.7. The box is lightly loaded: 40+ domains with 40-80 GB of traffic/month.
I recently installed munin and included in the default install was an entropy graph - to be specific:
/proc/sys/kernel/random/entropy_avail
On my box that value was consistently between 100 and 200. I seemed to remember that was an order of magnitude too low and after a bit of research, I found a blog post that seemed to match my situation (except it was on a debian distro)
http://www.chrissearle.org/blog/technical/increase_entropy_26_kernel_linux_box
I posted my situation to the Centos5/Webhosting forum hoping to hear from some kernel whiz but have so far have not received a response. So I thought I would run this by the front line troops too.
This random/urandom business is rocket science to me so I want to make sure I don't inadvertently hose anything on the box while trying to improve the situation. The blog post above suggested using /dev/urandom (the non-blocking pseudo random number generator) to feed entropy into /dev/random by using the daemon meant to feed in entropy from a hardware random number generator (rngd). My trial fix was to use the command "rngd -r /dev/random -t15" which seems to work as advertised: the entropy pool is refilled every 15 seconds. What is a little odd about this is that the distro seems to not contain any init.d support for any setup like this. I did find the fedora version of the init script and can certainly hack that to create something I could feed into chkconfig to create a service if need be.
The problem is, I am not convinced that this is helping the problem because my munin entropy graph still shows the original low levels, albeit now with spikes to more acceptable levels. Using:
'watch -n 1 cat /proc/sys/kernel/random/entropy_avail'
I can see the entropy pool filling but then quickly emptying - something is constantly sucking /dev/random down. The likely suspects I can think of are : apache (SSL), bind (port randomization), exim (TLS), though any app that uses random in place of urandom could be the problem - there is a bit of (old) finger pointing at the exim and the gnu libraries on this point. Entropy spikes during the daily crons, but that could just be disk activity - one of my early experiments was to verify that "ls -alr /" pegged entropy_avail.
So in the end I don't have a clue. I do not currently see log tracks of any errors caused by this situation, but I am not sure I would recognize one if I tripped over it. I will tinker some more with the rngd timeout to see if I can achieve a higher average level, but I worry about diluting the quality of the /dev/random/
Any info, suggestions appreciated...
I recently installed munin and included in the default install was an entropy graph - to be specific:
/proc/sys/kernel/random/entropy_avail
On my box that value was consistently between 100 and 200. I seemed to remember that was an order of magnitude too low and after a bit of research, I found a blog post that seemed to match my situation (except it was on a debian distro)
http://www.chrissearle.org/blog/technical/increase_entropy_26_kernel_linux_box
I posted my situation to the Centos5/Webhosting forum hoping to hear from some kernel whiz but have so far have not received a response. So I thought I would run this by the front line troops too.
This random/urandom business is rocket science to me so I want to make sure I don't inadvertently hose anything on the box while trying to improve the situation. The blog post above suggested using /dev/urandom (the non-blocking pseudo random number generator) to feed entropy into /dev/random by using the daemon meant to feed in entropy from a hardware random number generator (rngd). My trial fix was to use the command "rngd -r /dev/random -t15" which seems to work as advertised: the entropy pool is refilled every 15 seconds. What is a little odd about this is that the distro seems to not contain any init.d support for any setup like this. I did find the fedora version of the init script and can certainly hack that to create something I could feed into chkconfig to create a service if need be.
The problem is, I am not convinced that this is helping the problem because my munin entropy graph still shows the original low levels, albeit now with spikes to more acceptable levels. Using:
'watch -n 1 cat /proc/sys/kernel/random/entropy_avail'
I can see the entropy pool filling but then quickly emptying - something is constantly sucking /dev/random down. The likely suspects I can think of are : apache (SSL), bind (port randomization), exim (TLS), though any app that uses random in place of urandom could be the problem - there is a bit of (old) finger pointing at the exim and the gnu libraries on this point. Entropy spikes during the daily crons, but that could just be disk activity - one of my early experiments was to verify that "ls -alr /" pegged entropy_avail.
So in the end I don't have a clue. I do not currently see log tracks of any errors caused by this situation, but I am not sure I would recognize one if I tripped over it. I will tinker some more with the rngd timeout to see if I can achieve a higher average level, but I worry about diluting the quality of the /dev/random/
Any info, suggestions appreciated...