Hello,
I'm running DA 1.657.
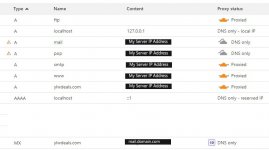
I'm currently using Gmail to retrieve e-mails from my server using POP3
This works perfectly for retrieval...
username: [email protected]
POP server: 1.2.3.4
Port: 110
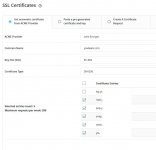
But now I want to make things more secure and use SSL.
So I tried the following:
username: [email protected]
POP server: 1.2.3.4
Port: 995
And add a checkmark beside 'Always use a secure connection (SSL) when retrieving mail.'
When Gmail tries to test this out it says:
Unable to establish secure SSL connection to 1.2.3.4
Server returned error: "SSL error: Leaf certificate is self-signed"
And if I run...
# openssl s_client -showcerts -connect 1.2.3.4:995
I do see:
Verify return code: 18 (self signed certificate)
At the bottom of the output.
directadmin.conf shows:
mail_sni=1
I'm just wondering if there is something I could look at to try and diagnose this problem.
Searching around for this issue on the DirectAdmin forums, everything I run across seems to be from many years ago.
Thank you
I'm running DA 1.657.
I'm currently using Gmail to retrieve e-mails from my server using POP3
This works perfectly for retrieval...
username: [email protected]
POP server: 1.2.3.4
Port: 110
But now I want to make things more secure and use SSL.
So I tried the following:
username: [email protected]
POP server: 1.2.3.4
Port: 995
And add a checkmark beside 'Always use a secure connection (SSL) when retrieving mail.'
When Gmail tries to test this out it says:
Unable to establish secure SSL connection to 1.2.3.4
Server returned error: "SSL error: Leaf certificate is self-signed"
And if I run...
# openssl s_client -showcerts -connect 1.2.3.4:995
I do see:
Verify return code: 18 (self signed certificate)
At the bottom of the output.
directadmin.conf shows:
mail_sni=1
I'm just wondering if there is something I could look at to try and diagnose this problem.
Searching around for this issue on the DirectAdmin forums, everything I run across seems to be from many years ago.
Thank you