Thanks jamgames2 and Zhenyapan! And of course a big thanks again to Richard.
I've taken all of the info from this thread and Richard's guide and compiled into the course of action I'll be taking.
If I've screwed anything up, missed anything, or doing anything in the wrong order, please let me know!
Step 1: Set the hostname via SSH
Via SSH as root:
# hostnamectl set-hostname server.primarydomain.com
- Now check your /etc/hostname file and make sure server.primarydomain.com is there.
If not, adjust it.
- Check your /etc/hosts file and make sure it contains this info:
127.0.0.1 localhost.localdomain localhost
your.ip.ad.res server.primarydomain.com server
Step 2: Reboot your server and then issue these commands to make sure they return the correct hostname.
# hostname
# hostname -f
Both commands should return: server.primarydomain.com
Step 3: Now go into the DA control panel and change the hostname to server.primarydomain.com
Admin -> Server Manager -> Administrator Settings -> Server Settings
Server's Hostname:
change from
www.primarydomain.com to server.primarydomain.com
Step 4: Create DNS records on the server for server.primarydomain.com
and the directory for it under /etc/virtual
Admin -> Server Manager -> DNS Administration -> Add DNS Zone
- First check to see if server-xx-xx-xx-xx.da.direct exists.
If it does, delete it.
- Now add the DNS Zone:
domain: server.primarydomain.com <-- no period
ip address: ip.add.re.ss
ns1.primarydomain.com <-- no period
ns2.primarydomain.com <-- no period
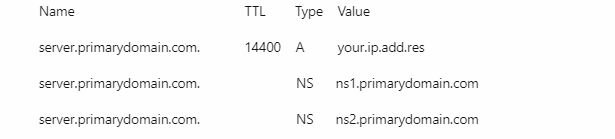
- Now go into the DNS Zone: server.primarydomain.com
You should see these records (in addition to the records that are already there. Leave those additional records there)
Name TTL Type Value
server.primarydomain.com. 14400 A ip.add.re.ss
server.primarydomain.com. NS ns1.primarydomain.com. <-- period at end
server.primarydomain.com. NS ns2.primarydomain.com. <-- period at end
- Due to a bug, you need to login via SSH and go to the /etc/virtual directory and
make sure that the directory server.primarydomain.com exists.
^^ I did not encounter this bug, the directory was there.
If not, create it and chown it to mail:mail
And set the permissions to 711
# cd /etc/virtual
# mkdir server.primarydomain.com
# chown mail:mail server.primarydomain.com
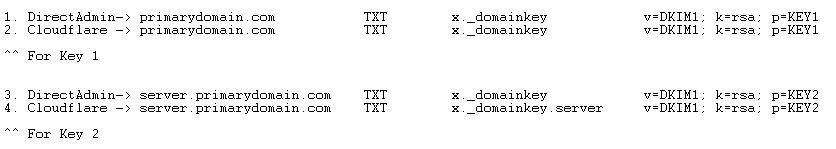
Step 5: Create a DKIM record for the hostname and copy the records to Cloudflare
cd /usr/local/directadmin/scripts
./dkim_create.sh server.primarydomain.com
- If all is correct it will create the same DKIM record as in your primarydomain.com
But you should check to make sure it's correct (in my case it was not, no idea why)
- In the end, between DirectAdmin and CloudFlare you're trying to achieve this:
The only kind of tricky part is copying the 'server.primarydomain.com' key to Cloudflare.
It goes under CloudFlare -> PrimaryDomain.com -> but the 'Name' of the Cloudflare record should be: x._domainkey.server
Step 6: CloudFlare
- Add an A record for server.primarydomain.com
Disable the Proxy (set to 'DNS only')
^^ Wondering if maybe the CloudFlare step should be done earlier, like right after Step 1. Can't hurt anything?
- If you use CloudFlare as external DNS, I would suggest for the primary domain to also copy the SPF and DKIM TXT records.
Step 7: Ask owner of the Server IP Address (Webhost) to add a PTR / Reverse DNS record for IPv4 and IPv6
Hello,
Please add a PTR / Reverse DNS record for my IPv4 address: A.B.C.D
And point it to: server.primarydomain.com.
And please add one for my IPv6 address as well: y:y:y:y:y:y:x.x.x.x.
Step 8: Once the PTR / Reverse DNS records have been added
Wait about a half hour for the hostname to resolve.
# nslookup [server ip address]
It should resolve to server.primarydomain.com
- Now you can request a new SSL certificate for your hostname.
cd /usr/local/directadmin/scripts
./letsencrypt.sh request_single server.primarydomain.com 4096
- Once you have a certificate for your hostname, you can turn on ssl=1 in directadmin.conf
Step 9: Now let's see what happens when I run:
# openssl s_client -showcerts -connect ip.ad.dre.ss:995
Woo hoo! Success. No more 'self signed' certificate.
And Gmail now approves of my POP3 mail server over Port 995.
Be sure to use: server.primarydomain.com
And not your IP address.
If I've screwed anything up, missed anything, or in the wrong order, please let me know!
Thank you